While taking this Pluralsight learning path, I did the setup required to enable client access to mailboxes on Microsoft Exchange Server.
In order for the Outlook client to trust the Exchange server I needed to setup a certificate that the Exchange server will use.
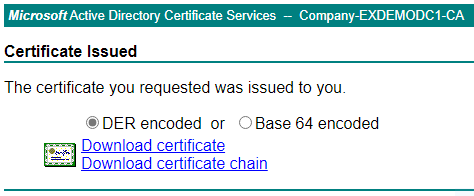
Download the issued certificate
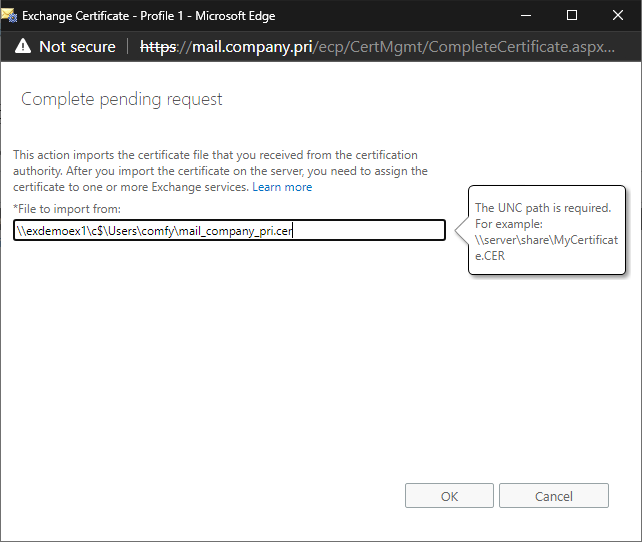
Complete the certificate request
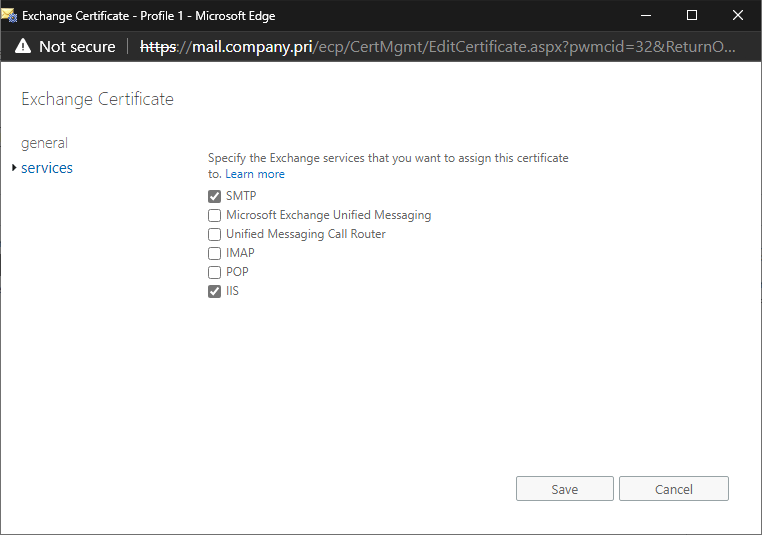
Setup the Exchange services that should use the certificate
Second, I setup Exchange to use Kerberos authentication as to eliminate the situation where many or all clients are connecting to one Exchange server to perform authentication. This way Outlook contacts a domain controller and gets issued a certificate that is then used to authenticate with the Exchange server.
This PowerShell command allows the shared service computer account to use AES encryption. This account will be used by the Exchange server.
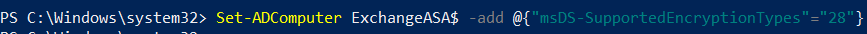
In the command window below I perform all the remaining steps to have Exchange use Kerberos
- The service account password is shared with the Exchange server
- Then I verify that the alternate service account configuration has been applied
- Then I create the service principal names for the Exchange client namespaces: mail and autodiscover. This will ensure the Outlook client will get a ticket from the domain controller for the alternate service account instead of the hostname of the exchange server
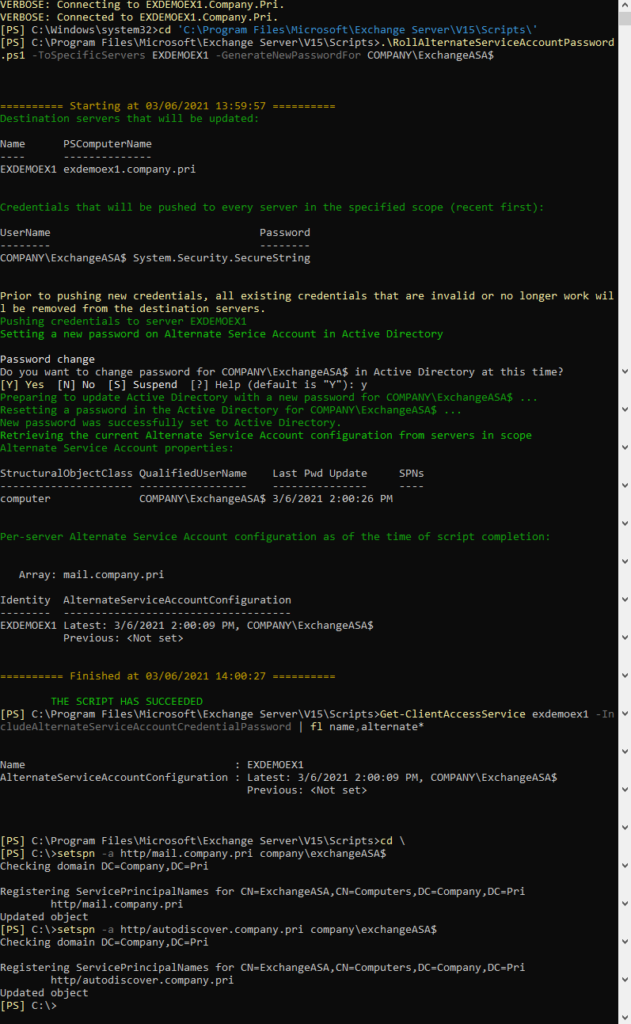
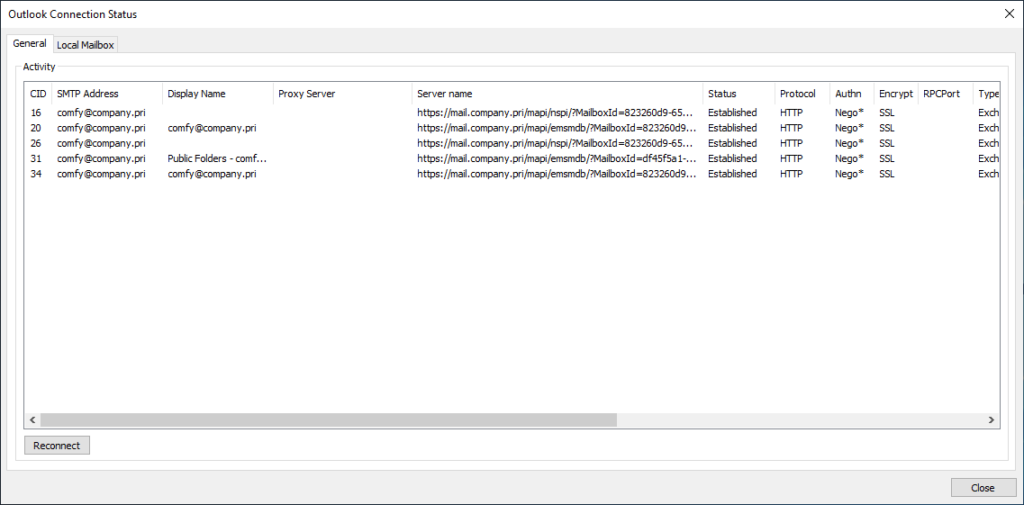
This is what the user experience looks like when opening Outlook for the first time. There are no authentication errors and autodiscover is able to find their email account as it matches their user principal name in the domain.
Also the Outlook client is using the correct client access namespace.
And that’s it for this post. Thank you for reading!
Hey gamers! Been checking out rio66.bet trực tuyến lately. Good vibes and lots of stuff to do. Click here: rio66.bet trực tuyến
Yo! Just had a blast on red 88.vip. Good times and smooth gameplay. You should give it a looksie: red 88.vip
3kingbet, huh? Sounds regal. Let’s see if I can win a kingdom! Putting my crown on and heading over! Check it out: 3kingbet
[1608]ta7777 Casino: Best PH Slots, Login & Register. Download the ta7777 APK Today! Join ta7777 Casino for the best PH slots! Experience easy ta7777 login & register options. Get the ta7777 download apk today to play the latest ta7777 slot games! visit: ta7777
[5545]fc178 Casino Philippines: Top Slots, Easy Register, Login & App Download Join fc178 Casino Philippines for the ultimate gaming experience! Enjoy fast fc178 register and fc178 login to access premium fc178 slot games. Get the fc178 download app today and start winning at the #1 fc178 casino. visit: fc178
[5732]684casino Official Site: Best Online Slots Philippines – Easy Login, Register, and App Download Join 684casino official site for the best online slots Philippines. Fast 684casino login, easy 684casino register, and 684casino app download. Win big today! visit: 684casino
[3452]Betraise Online Casino Philippines: Best Slots, App Download, Login & Register Join Betraise Online Casino Philippines for top Betraise slots. Quick Betraise login & register. Get the Betraise app download and start winning in the PH today! visit: Betraise
[8579]No1JL: Best Online Casino in Philippines – Easy No1JL Login, Register & App Download for Top Slot Games Experience No1JL, the premier online casino in Philippines! Quick No1JL login, register & No1JL app download for top No1JL slot games. Join the #1 platform today! visit: no1jl
[6700]GGBet Philippines: Quick Login & Register. Get the App Download to Play Online Slots with a Massive Casino Bonus. Join GGBet Philippines! Experience quick GGBet login and register options to play top GGBet online slots. Get the GGBet app download to claim your massive casino bonus today! visit: GGBet
[9311]99boncasino: The Best Online Slots and GCash Casino in the Philippines visit: 99boncasino
[7130]SSBET777 Online Casino Philippines: Easy Login, Register, & App Download for the Best Slot Games. Join SSBET777 Online Casino Philippines! Fast ssbet777 login & register to play the best ssbet777 slot games. Get the ssbet777 app download and win big today! visit: ssbet777
[4170]99bon Login: Official 99bon Slot, Register & Download App Philippines. Access the Best 99bon Link Alternatif for Secure Casino Gaming. Official 99bon Login: Experience the best 99bon slot games in the Philippines. Easy 99bon register process for new players! Access our secure 99bon link alternatif and 99bon download app for a premium, secure mobile casino experience. Join the #1 platform for top-tier rewards and reliable gaming today. visit: 99bon
[3494]JL56 Online Casino Philippines: Secure Login, Easy Register, and App Download for the Best Slot Games Join JL56 Online Casino Philippines for premium gaming. Secure jl56 login, easy jl56 register, and jl56 app download for the best jl56 slot games. Start winning now! visit: jl56
[7702]jl18 giris|jl18 login|jl18 app|jl18 casino|jl18 slots Experience the ultimate thrill at jl18, the Philippines’ premier online gambling destination. Secure your jl18 login today to enjoy a wide variety of jl18 slots and premium jl18 casino games. Download the jl18 app for seamless mobile play and enjoy fast jl18 giris access to big wins and top-tier entertainment! visit: jl18
[6110]Kingclub Official Casino Philippines: Login, Register & Download App for Premium Slot Online Games. Experience premium gaming at Kingclub Official Casino Philippines. Kingclub login or kingclub register today to play top kingclub slot online games. Kingclub download app for ultimate mobile wins! visit: kingclub
[5690]jiliko747 download|jiliko747 app|jiliko747 slots|jiliko747 casino|jiliko747 login Join jiliko747 casino, the top Philippines gaming site. Get the jiliko747 app via download, use your jiliko747 login, and play premium jiliko747 slots to win today! visit: jiliko747
[1735]711php Online Casino Philippines: Top Slot Games, Easy Register & Login, and Official App Download. Join 711php Online Casino Philippines for top 711php slot games. Experience easy 711php register and 711php login processes. Secure the official 711php app download for mobile play. Start winning today at the premier 711php online casino! visit: 711php
[3943]Pinas77: The Best Online Casino in the Philippines. Login, Register, and Play Pinas77 Slot or Download the App Today! Experience Pinas77, the best online casino in the Philippines! Quick Pinas77 login and register to play top Pinas77 slot games. Download the Pinas77 app today! visit: pinas77
[9721]JLJL44 Official Link: Best Slot Online in Philippines. Login, Register, and Download App to Win Today! Visit the jljl44 official link for the best slot online in Philippines. Complete your jljl44 login or jljl44 register today. jljl44 download app and win now! visit: jljl44
[2954]King Login & Register: Play King Slot Online and Download the King App & Casino APK for the Best Gaming Experience in the Philippines. Experience King, the top choice for gaming in the Philippines. Fast king login & king register to play king slot online. Download king app & king casino apk now! visit: king
[7948]Pesomax Online Casino Philippines: Top Slot Games, Easy Register, Login & App Download. Experience Pesomax Online Casino Philippines! Enjoy top-rated Pesomax slot games with a quick Pesomax register and login process. Secure your Pesomax app download today for the best mobile gaming experience. Join the #1 online casino in the Philippines and start winning now! visit: pesomax
[9779]TTJL Online Casino Philippines: Official TTJL Login, Register & App Download for Premium TTJL Slots. Experience the ultimate gaming at TTJL Online Casino Philippines. Access your official TTJL login, fast TTJL register, and TTJL app download for premium TTJL slots and big wins. Join the most trusted online casino in the PH today! visit: ttjl
[5035]mwcbet register|mwcbet login|mwcbet casino|mwcbet giris|mwcbet app Join MWCBet, the Philippines’ premier online casino platform. Complete your MWCBet register and login (giris) today to access a wide range of premium MWCBet casino games, including slots and live dealers. Download the MWCBet app for a seamless mobile gaming experience and start winning with the most trusted casino in PH! visit: mwcbet
[1726]Jili7 Online Casino Philippines: Easy Jili7 Login, Register, and App Download for Premium Jili7 Slot Games. Join Jili7 Online Casino Philippines for premium Jili7 slot games. Easy Jili7 login, quick Jili7 register, and secure Jili7 app download. Play at the best Jili7 casino online today! visit: jili7
[1719]Jili333 Login & Register: Top Philippines Online Slot & Casino App Download Experience the ultimate gaming at Jili333! Secure your jili333 login or complete your jili333 register to play the best Philippines online slots. Enjoy premium jili333 slot games, fast jili333 casino login, and get the official jili333 app download for a seamless mobile experience. Join now! visit: jili333
[2802]GBet Online Casino PH: Official GBet Login, Register & App Download for Premium Slots Experience premium gaming at GBet Online Casino PH! Access the official GBet login, GBet register for free, or start your GBet app download to play top GBet slots. visit: gbet
[7763]Magicjili: Top Philippines Online Slots & Casino App. Secure Magicjili Login, Register & App Download for the Best Gaming Experience. Experience the best Philippines online slots at Magicjili. Secure Magicjili login, register, and Magicjili app download to enjoy our premium casino app today! visit: magicjili
[4302]jiliph casino|jiliph slots|jiliph register|jiliph download|jiliph login Experience the ultimate online gaming at jiliph casino, the Philippines’ top destination for premium entertainment. Complete your jiliph register today to enjoy top-tier jiliph slots, seamless jiliph login, and the latest jiliph download for mobile play. Join now and start winning! visit: jiliph
[1996]fbjili giris|fbjili download|fbjili register|fbjili slots|fbjili login Experience the best online gaming at fbjili, the Philippines’ top casino platform. Join today for easy fbjili register and fbjili login to play premium fbjili slots. Get the fbjili download for mobile access and start your fbjili giris to enjoy secure betting and massive rewards! visit: fbjili
[2394]Winph8 Online Casino Philippines: Secure Winph8 Login, Fast Register & App Download for Premium Slot Games. Join Winph8 Online Casino Philippines for premium Winph8 slot games. Enjoy a secure Winph8 login, fast Winph8 register, and easy Winph8 app download. Experience the ultimate gaming platform and start winning today! visit: winph8
[2670]39 Casino Philippines: Official 39 Login, Slot & Register. Download Now for the Best Online Gaming Experience. Experience the best online gaming at 39 Casino Philippines. Quick 39 login, premium 39 slot games, and easy 39 register. 39 download the app now to start winning today! visit: 39
[2067]365jl Official Link: Fast 365jl Login, Register & App Download for Top 365jl Slot Games in the Philippines. Join 365jl, the top online casino in the Philippines! Use our 365jl official link for fast 365jl login, easy 365jl register, and 365jl app download. Experience premium 365jl slot games and start winning big today! visit: 365jl
[496]777pub Online Casino Philippines: Login, Register, and App Download for Premium Slots Experience the best at 777pub Online Casino Philippines. 777pub login or 777pub register now to play premium 777pub slots. Get the 777pub app download for 24/7 mobile fun! visit: 777pub
[5536]WJPESO: The Best Online Casino in the Philippines. Easy Login, Register & App Download for Premium Slots and Big Wins. Experience WJPESO, the best online casino in the Philippines. Secure WJPESO login and register to enjoy premium WJPESO slots and big wins. Start your WJPESO app download now for a premium gaming experience anytime, anywhere! visit: wjpeso
[21]jljl3355 login|jljl3355 app|jljl3355 casino|jljl3355 giris|jljl3355 slots Experience the ultimate online gaming at jljl3355 casino, the premier destination for Philippines players. Access your account via jljl3355 login or jljl3355 giris to enjoy a massive selection of jljl3355 slots and live dealer games. For seamless mobile action, download the jljl3355 app today and start winning with secure payouts and exclusive bonuses! visit: jljl3355
[7057]PH22: The Most Trusted and Legit Online Casino in the Philippines – Register & Login Today! visit: ph22login
[8687]Jilliko Casino Philippines: Best Jilliko Slot Games, Easy Login, Register & Official App Download Experience the best Jilliko slot games at Jilliko Casino Philippines! Secure Jilliko login, easy Jilliko register & official Jilliko download. Join the top Jilliko casino and start winning big today! visit: jilliko
[3469]W19 Casino Philippines: The Best Legit Online Gambling & Slots via GCash Experience W19 Casino Philippines, the premier destination for the best online gambling PH has to offer. Secure your w19 login registration today to enjoy a legit online casino GCash experience featuring high-payout w19 slots and live casino games. Join the most trusted and reliable gaming platform in the Philippines for seamless transactions and elite entertainment. visit: w19
[2910]kkkjili Casino Philippines: Your Premier Destination for kkkjili Slot Games. Quick kkkjili Register, Easy kkkjili Login, and Fast kkkjili Download for the Ultimate Gaming Experience! Experience kkkjili Casino Philippines! Quick kkkjili register & easy kkkjili login for top kkkjili slot games. Fast kkkjili download for the ultimate gaming experience. Join now! visit: kkkjili
[7058]Gameroom777 Philippines: Login, Register, and Download APK for the Best Online Slots Experience. Experience the ultimate online slots at Gameroom777 Philippines. Easy gameroom777 register and login! Download the gameroom777 apk now for the best mobile gaming. visit: gameroom777
[526]Wagibet931: Login & Daftar Slot Gacor Terpercaya. Download APK Wagibet931 & Link Alternatif Resmi Terbaru. Wagibet931 adalah platform slot gacor terpercaya di Philippines. Segera daftar & login Wagibet931 untuk menang besar. Download APK Wagibet931 & akses link alternatif resmi terbaru sekarang! visit: wagibet931
[1039]The Philippines’ Leading GCash Online Casino and Official Betting Platform visit: phtaya1
[8272]ah77 Login & Register: Top Online Slot Casino in the Philippines. Download Now & Get the Latest Link Alternatif. Join ah77, the #1 online slot casino in the Philippines. Easy ah77 login & register. Get the ah77 download and latest link alternatif to play top ah77 slot games now! visit: ah77
[3230]VVJL Login & Register | Download VVJL Slot App APK – Official Casino Link PH Experience the ultimate gaming thrill at VVJL! Access the official VVJL casino link to complete your VVJL login and register. Download the VVJL slot app APK today for the best casino games in the PH. Join now and win big! visit: vvjl
[3002]Phpfamous: Best Slot Gacor Philippines. Login, Register, & Download APK for Real-Time RTP Live & Big Wins! Join Phpfamous, the best slot gacor in the Philippines! Login, register, or download the APK for real-time RTP live data and your chance at big wins. Play now! visit: phpfamous
[1814]Tongitstok Online Casino: Easy Login, Register & App Download for the Best Slot Games in the Philippines. Join Tongitstok Online Casino, the Philippines’ premier destination for gaming. Enjoy seamless tongitstok login, quick tongitstok register, and the tongitstok app download for the best tongitstok slot games. Experience secure, high-payout online casino action and start winning today! visit: tongitstok
[2080]Wagibet: Trusted Philippines Online Casino. Access Wagibet Login, Wagibet Daftar, and Wagibet Slot Gacor. Use our Wagibet Link Alternatif or Download APK now! Wagibet: The most trusted Philippines online casino. Access Wagibet login, Wagibet daftar, and high-win Wagibet slot gacor. Use our Wagibet link alternatif or download apk for the ultimate mobile gaming experience today! visit: wagibet
[8524]WJSLOT: Official Slot Gacor Site, WJSLOT Login & Register. Access Link Alternatif and Download APK for the Best Philippines Casino Experience. Experience the best Philippines casino at WJSLOT, the official slot gacor site. Easy WJSLOT login & register, access link alternatif, and download APK for big wins! visit: wjslot
[1854]JI777 Casino Philippines: Login, Register, and Play Best Slots | JI777 App Download Join JI777 Casino Philippines for the ultimate gaming experience. Secure JI777 login & easy register to play premium JI777 slots. Get the JI777 app download now! visit: ji777
[2991]BoVegas Casino Philippines: Top Online Slots & Exclusive Bonuses. Access BoVegas Casino Login, Sign Up Today, or start your BoVegas App Download for the ultimate gaming experience. Join BoVegas Casino Philippines for top online slots! Access BoVegas Casino Login, Sign Up, or BoVegas App Download to claim your exclusive BoVegas Casino Bonus. visit: BoVegas
[9907]PHBest Online Casino: Official Login, Register & App Download for Premium Slot Games in the Philippines. Experience the ultimate gaming at PHBest Online Casino! Get your official phbest login, complete your phbest register, and get the phbest app download to enjoy premium phbest slot games in the Philippines. Join the top-rated platform for secure play and big wins today! visit: phbest
[4787]Jili0 Casino Philippines: Experience the Best Jili0 Slot Games. Quick Jili0 Login, Register, & App Download for Premium Online Gaming. Experience the best Jili0 slot games at Jili0 Casino Philippines. Fast Jili0 register, quick Jili0 login, and Jili0 download for premium mobile gaming. Play now! visit: jili0
[1425]Peso88 Online Casino: Secure Login, Easy Register & App Download for the Best Slot Games in the Philippines. Join Peso88 Online Casino for the best gaming in the Philippines. Enjoy secure peso88 login, easy peso88 register, and peso88 app download. Play top peso88 slot games and win today! visit: peso88
[9657]SLVIP Casino: The Best Philippines Slot Games, Easy Login, Register & App Download Experience SLVIP Casino, the home of top Philippines slot games! Fast slvip register and slvip login to start winning. Try your favorite slvip slot or get the slvip download app now for the ultimate mobile gaming experience. visit: slvip
[3663]1plusgame: Top Slot Online in the Philippines. Easy Login, Register, and Download App via Official Link. Experience 1plusgame, the top slot online in the Philippines. Use our official link for fast 1plusgame login, easy register, and 1plusgame download app. Join and win now! visit: 1plusgame
[6411]PH365 Online Casino Philippines: Quick PH365 Login & Register, Exciting PH365 Slot Games, and Official App Download. Join PH365 Online Casino for the best PH365 slot games in the Philippines. Enjoy fast PH365 login & register access. Get the official PH365 app download and start winning today! visit: ph365
[776]The Best Legit Online Casino in the Philippines for Slots and More at 668jili visit: 668jili
[9264]fb7777: The Best Legit Online Casino Philippines for GCash Slots & Sports Betting Join fb7777, the best online casino Philippines GCash users trust for legit online gambling. Register via fb7777 login registration for top slots and sports betting today! visit: fb7777
[2415]58jili Casino Philippines: Best Online Slots, Easy Login, Register & App Download Experience the best online slots at 58jili Casino Philippines! Enjoy a fast 58jili login, easy 58jili register, and 58jili app download. Play your favorite 58jili slot games and win big today. visit: 58jili
[6068]phtaya06: The Premier Online Casino and Best Gambling Experience in the Philippines visit: phtaya06
[2487]jlfff Online Casino Philippines: Login, Register & App Download for Top Slots Join jlfff Online Casino Philippines! Quick jlfff login & jlfff register to play premium jlfff slot games. Get the jlfff app download now for the best mobile casino experience. visit: jlfff
[4075]PHL163: The Best Online Casino in the Philippines for Legit Slot Games and GCash Payouts. Register Now for an Exclusive Bonus! Join PHL163, the best online casino Philippines for legit slot games and fast GCash payouts. Visit PHL163 login official now to claim your exclusive register bonus! visit: phl163
[7872]KingPH Online Casino Philippines: Experience top-tier slot games. Secure KingPH login, quick register, and official KingPH app download for the ultimate gaming experience. Join KingPH Online Casino Philippines for premium KingPH slot games. Experience a secure KingPH login, fast KingPH register, and official KingPH app download today! visit: kingph
Alright, so I downloaded this phswerteapp thing. It’s kinda neat, though not my usual jam. If you’re into the stats and stuff, might be your thing. Give it a whirl, could surprise ya. Download it here: phswerteapp
Taya99comlogin, what up! Getting logged in is pretty smooth, no major hassles. Games are decent. I’ve seen better, but I’ve also seen way worse. Definitely worth a peek for a quick round. Peep it: taya99comlogin
Yo, 5161bet! Been trying my luck here lately. The site’s alright, easy enough to navigate. Could use a few more promos, but hey, who am I to complain when I win, right? Check it out: 5161bet